© 2011 by Nick B. Nicholaou, all rights reserved President, Ministry Business Services, Inc. Reprinted from CTI’s Managing Your Church (www.managingyourchurch.com)
Every year more organizations and people fall victim to cybercrime. Last year more than 300,000 reported cybercrimes to the FBI with losses in the hundreds of millions of dollars. Whether it’s simple theft, fraud, or identity theft, this is a significant area of opportunity for criminals. Let’s shed some light on how to protect your church office and those you know from cybercrime.
Where There’s Opportunity…
A new level of crime became possible with the popularity of the Internet on a scale never before imagined! Criminals saw the opportunity to repackage old scams into electronic format and reach the masses in a way that could yield astounding results. That criminal vision has become a painful reality to many naïve victims.
The FBI co-publishes an annual Internet Crime Report, detailing the painful statistics. In the 2010 Report:
- Among people ages 20 and older, fraud complaints are evenly distributed. This means those who are younger and more tech savvy still are just as likely to fall victim.
- Cybercrimes are evenly split among male and female victims, though men report an average of 25% more in financial losses.
- The largest complaint category was no payment or no delivery of merchandise through an online transaction (14%), followed by scams (13%) and identity theft (10%).
- The top five places where criminals resided was USA (66%), UK (10%), Nigeria (6%), China (3%), and Canada (2%).
This means we’re all vulnerable, especially in the United States where it appears most of the crimes occur.
It is important to note that people are vulnerable, but so are organizations! If your church or ministry conducts business over the Internet (email, purchasing, etc), it is probably more vulnerable than an individual because of the number of staff online!
Most Common Scams
While non-delivery of merchandise or payments was the largest category of complaints, the second was scams. The three most common 2010 scams, according to the Report, are:
- Mystery/ Secret Shopper. Victims are contacted via email to help retailers evaluate the quality of their stores, personnel, and processes. Sometimes the employing company sends a check and asks the person to cash the funds, spend them, and return the unused portion. The problem is that the check is counterfeit. Sometimes the employing company uses an extensive application and screening process to gain the shopper’s personal account and identity information.
- Claims of Being Stranded. Law firms are getting email from out-of-country citizens needing help. Also, people receive emails telling them their friend or family member is stranded and needs money immediately wired to them (in some cases the email arrives from a person they know whose email account was hacked). The please are designed to trick people into sending money.
- Natural Disaster Relief. Natural disasters bring out the best in Americans; they also bring out criminals.
What Does the FBI Recommend?
The FBI provides five quick recommendations that individuals and church offices should note and share:
- Do not respond to unsolicited email, also known as spam.
- Avoid filling out forms in emails.
- Don’t click links
- Don’t open attachments in unsolicited email.
- Be skeptical of those representing themselves as surviving victims or stranded friends.
Extra Precautions
The FBI’s recommendations are good, but I suggest going further with these additional precautions:
- Besides avoiding responses to unsolicited email, get your email scanned for spam and malware before it gets to your computers. This will eliminate almost all undesirable email and improve your defenses, but continue to be cautious! Cybercriminals are constantly working on ways to get through those protections, so still be wary of anything that looks questionable.
- Any email offers that sound fantastic (another way of saying too good to be true) are probably scams. Immediately delete them.
- When you or your office want to respond disaster-relief fundraisers, give only to organizations you know. Research unfamiliar ones through Charity Navigator or Evangelical Council for Financial Accountability (www.ecfa.org).
Shopping Online
Shopping online is a convenient and effective way to secure needed resources, often while saving money. For anyone using a church computer to make purchases, the following basic best practices before entering personal information, credit card, or banking information can help ensure the transactions remain safe:
Windows Explorer
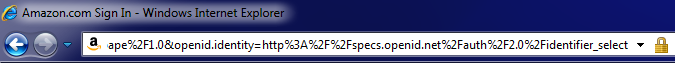
When browsing in Internet Explorer (the picture above is from version 8), first look for the closed lock. This tells you whether or not you’re on a secure encrypted web page. If you’re still uncertain, click on the lock; doing so will tell you who owns the security certificate, who the issuing authority is, and when it expires.

On a Mac

In Firefox (the picture above is from version 7) the security certificate is available via the color-shaded section to the left of the website address (also called the URL). Clicking on that shaded area shows the dark box shown above with summary information about the certificate; clicking on More Information shows the following:

Clicking on View Certificate shows the following:

